1 Centos7.6集群实现OPENLDAP认证
1.1 LDAP简介
LDAP 全称轻量级目录访问协议(英文:Lightweight Directory Access Protocol),是一个运行在 TCP/IP 上的目录访问协议。目录是一个特殊的数据库,它的数据经常被查询,但是不经常更新。其专门针对读取、浏览和搜索操作进行了特定的优化。目录一般用来包含描述性的,基于属性的信息并支持精细复杂的过滤能力。比如 DNS 协议便是一种最被广泛使用的目录服务。
LDAP 中的信息按照目录信息树结构组织,树中的一个节点称之为条目(Entry),条目包含了该节点的属性及属性值。条目都可以通过识别名dn来全局的唯一确定,可以类比于关系型数据库中的主键。比如dn为uid=test,ou=People,dc=sugon,dc=com的条目表示在组织中一个名字叫做test的员工,其中uid=test也被称作相对区别名rdn。
一个条目的属性通过LDAP元数据模型(Scheme)中的对象类(objectClass)所定义,下面的表格列举了对象类inetOrgPerson(Internet Organizational Person)中的一些必填属性和可选属性。
| 属性名 | 是否必填 | 描述 |
|---|---|---|
| cn | 是 | 该条目被人所熟知的通用名(Common Name) |
| sn | 是 | 该条目的姓氏 |
| o | 否 | 该条目所属的组织名(Organization Name) |
| mobile | 否 | 该条目的手机号码 |
| description | 否 | 该条目的描述信息 |
下面是一个典型的LDAP目录树结构,其中每个节点表示一个条目。在下一节中我们将按照这个结构来配置一个简单的LDAP 服务。
1.2 LDAP服务端安装配置
1.2.1 安装phpldapadmin
1 | yum -y install httpd php php-ldap php-gd php-mbstring php-pear php-bcmath php-xml |
- 重启http服务器
1 | systemctl enable httpd.service |
1 | sed -i "s#^\$servers->setValue('login','attr','uid');#//\$servers->setValue('login','attr','uid');#g" /etc/phpldapadmin/config.php |
- 通过浏览器登录http://10.0.50.100/ldapadmin

1.2.2 安装配置openldap
- 关闭防火墙,关闭selinux
1 | sed -i '/SELINUX/s/enforcing/disabled/' /etc/selinux/config && setenforce 0&& systemctl disable firewalld.service && systemctl stop firewalld.service |
- 安装openladp服务
1 | yum -y install openldap compat-openldap openldap-clients openldap-servers openldap-servers-sql openldap-devel migrationtools |
- 设置日志文件
1 | mkdir /var/log/slapd |
- 配置安装文件
1 | cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG |
- 启动ldap
1 | systemctl start slapd |
- 导入基本的模板
1 | ls /etc/openldap/schema/*.ldif | while read f; do ldapadd -Y EXTERNAL -H ldapi:/// -f $f; done |
- 导入成功日志文件
1 | SASL/EXTERNAL authentication started |
配置basedn
olcSuffix —— 数据库后缀,它是LDAP服务器提供信息的域名。简单来说,它应该更改为域名。
olcRootDN —— 一般指的是root用户,具有所有访问权限的用户
olcRootPW —— RootDN的密码olcLogLevel—— 日志的收集
1 | dn: olcDatabase={1}monitor,cn=config |
1 | ldapmodify -Y EXTERNAL -H ldapi:/// -f base.ldif ###添加basedn |
- 设置工作目录
1 | dn: dc=sugon,dc=com |
- 设置允许普通用户修改自己的密码
1 | dn: olcDatabase={2}hdb,cn=config |
- 设置memberof
1 | dn: cn=module{0},cn=config |
- ldap服务端性能调优
1 | dn: cn=config |
- 增加查询索引,加快查询速度
1 | dn: olcDatabase={2}hdb,cn=config |
- 增加数据库缓存容量,加速数据读写
1 | dn: olcDatabase={2}hdb,cn=config |
- 系统用户迁移工具
1 | yum install migrationtools -y |
1.3 openldap添加用户
- 编写自定义用户ldif文件
1 | dn: uid=yaolang,ou=People,dc=sugon,dc=com |
- 编写自定义用户组信息
1 | dn: cn=yaol,ou=Group,dc=sugon,dc=com |
1.4 LDAP客户端安装配置
1.4.1 客户端安装
1 | yum -y install openldap-clients nscd authconfig nss-pam-ldapd |
1.4.2 客户端配置
- 客户端注册到LDAP服务端上,10.0.50.100是LDAP服务端的IP地址
1 | authconfig --enablesssd \ |
1.4.3 验证客户端正确性
1 | getent passwd yaolang |
- 登录进行验证
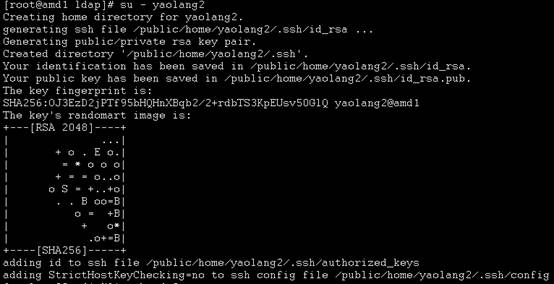
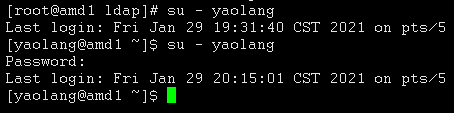
- 可以使用ldap密码进行认证
1.4.4 客户端用户密码验证
- 配置可以用密码进行验证
1 | sed -i 's/^auth[[:space:]]*substack[[:space:]]*password-auth/#&/' /etc/pam.d/sshd |
- 设置在ldap中查找用户名和利用ldap密码认证
1 | sed -i "s/sss/ldap/g" /etc/nsswitch.conf |
1.4.5 ldap相关客户端优化
1 | NSLCD_THREADS=3 |
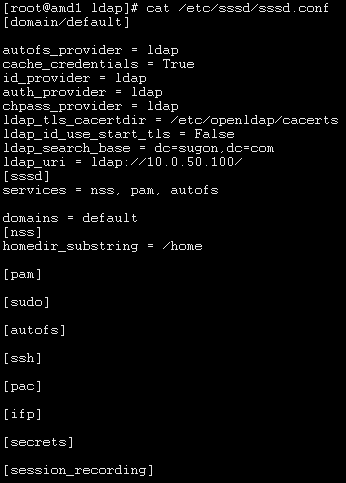
需要保证/etc/sssd/sssd.conf的内容正确性,否则会无法获取到用户信息